-
Persistent File Security
The Magic of FinalCode:
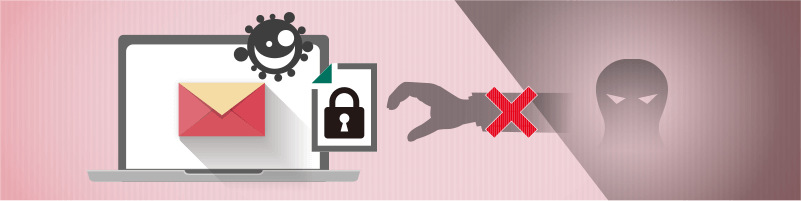
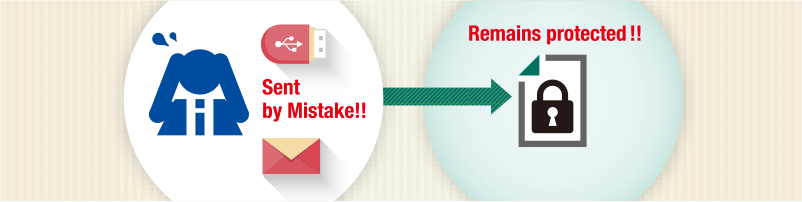
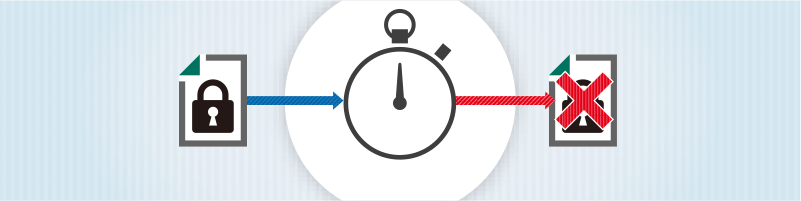
Make files disappear AFTER they are sent.Grant file access to authorized recipients,
audit activity throughout the lifecycle,
and modify security policies on demand.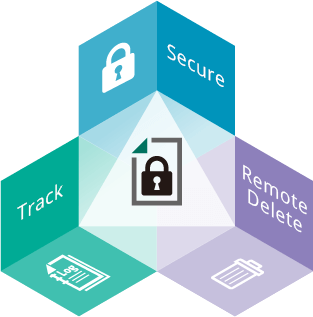
-
-
Secure
Restrict file access
Dynamic policy modification- No password
- Designate recipients
- Limit access count/duration
- Control
- Automatic file deletion on unauthorized access
- Print/screen watermark
-
Track
Persistently track file
activity throughout file lifecycle- Access log
- Unauthorized access detection
- System operation log
-
Remote Delete
Make files disappear
AFTER they are sent- Remote file deletion
- Remote policy modification
File Protection Software
-
FinalCode 6
FinalCode’s persistent file security solution is designed to enable businesses to easily protect shared sensitive files wherever they go within and outside their organization. FinalCode provides an extensive array of enterprise-grade file security features packaged in an easy to use, flexible and scalable eDRM platform.
-
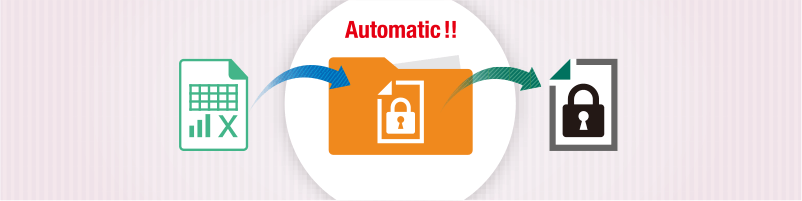
FinalCode for Box
FinalCode integrates with Box, an enterprise cloud collaboration platform, to not only automattically secure uploaded files but also track/modify permissions for files downloaded from the secure Box repository.
-
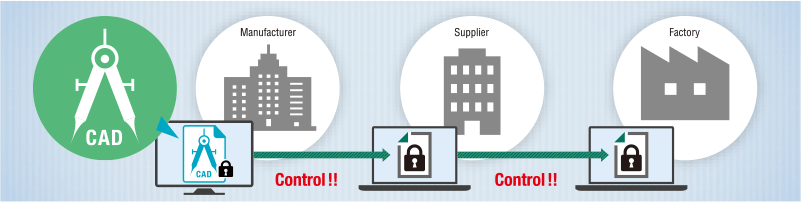
FinalCode for CAD
With FinalCode, you can share your sensitive 2-D and 3-D Computer Aided Design files with greater confidence and without hindering the collaborative process.
Use Cases
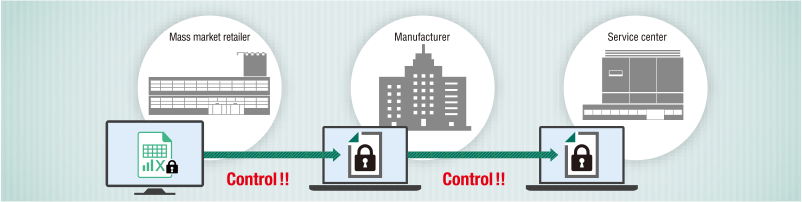
Protection from targeted attacks and preventing data breaches are just a few examples of why organizations want to secure sensitive information. FinalCode offers a range of features to meet every security requirement. Here are common use cases highlighting the combination of optional subscriptions that each organization selected to achieve persistent file security with FinalCode.